Zero Days CTF (2024) RE - 2
In this challenge, we'll explore binary analysis, focusing on binary file formats, executable packers, and static analysis techniques. We'll examine the structure of executables, how packers like UPX compress them, and how to unpack and analyze such binaries using tools like HxD, Detect-It-Easy, and Binary Ninja. Through this exploration, we'll uncover hidden information and potential flags within binary files.

The second challenge features the file ‘chall’.
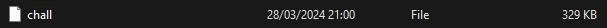
Upon observation in HxD, it is evident that the file is an ELF file. The identification of the file as an ELF file is attributed to the observed magic bytes.
An ELF (Executable and Linkable Format) file is a common binary file format used for executables, object code, shared libraries, and core dumps in Unix-like operating systems. It defines the structure for executable files, specifying how programs are laid out in memory and executed by the operating system loader or kernel. ELF files contain headers and sections that describe program information, such as code, data, symbols, and dynamic linking information. They are versatile and widely used across various Unix-based systems, including Linux and BSD.
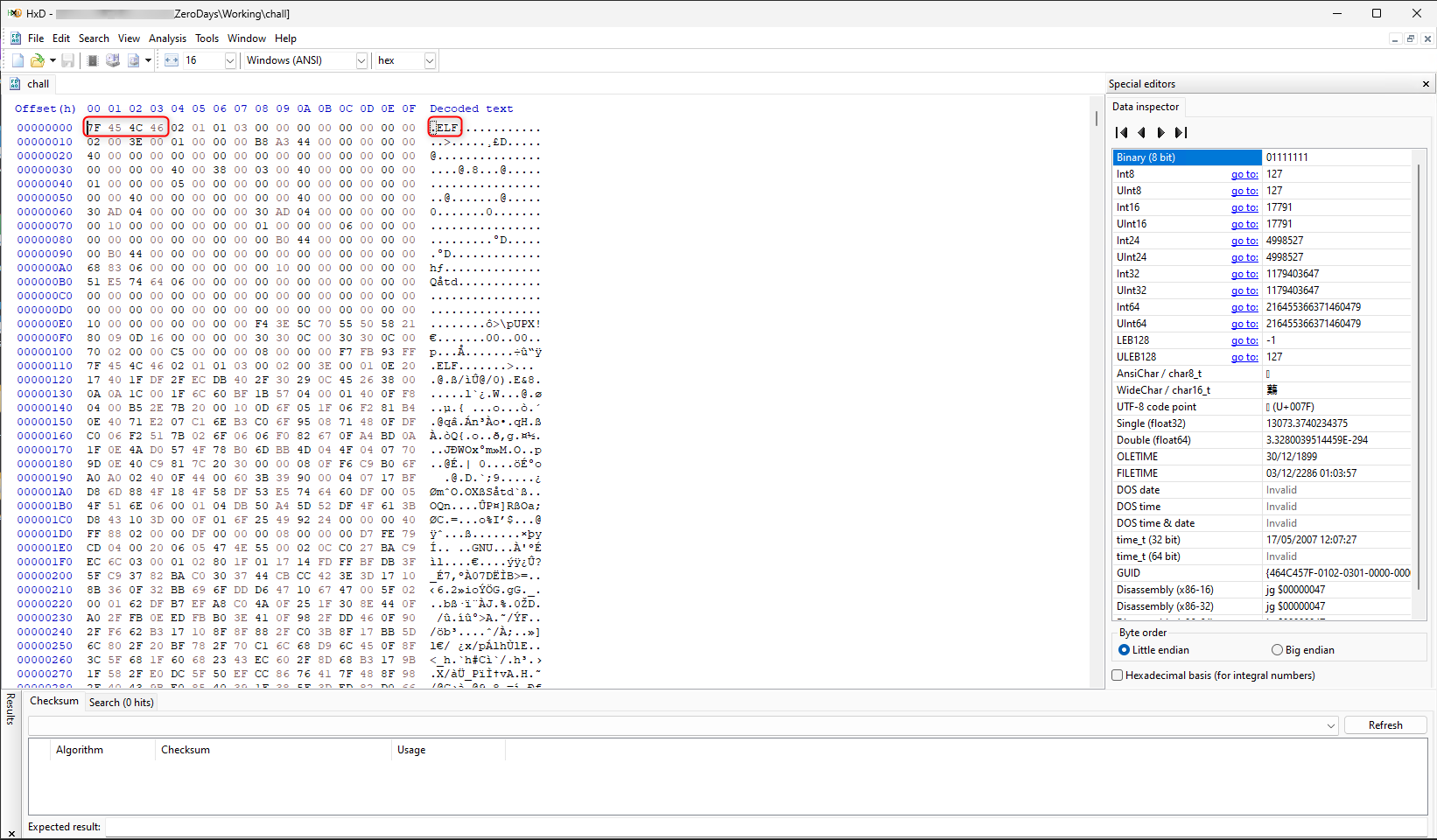
Using Detect-It-Easy, it is observed that the file is utilizing the UPX packer.
UPX (Ultimate Packer for eXecutables) is a free and open-source executable packer. It compresses executable files and libraries, reducing their size and making them more challenging to analyze or reverse engineer. UPX achieves compression by rearranging code sections, removing redundant data, and applying various compression algorithms. It is commonly used by software developers to reduce the size of their executables without compromising functionality. However, it is also utilized by malware authors to obfuscate their code and evade detection by security software.
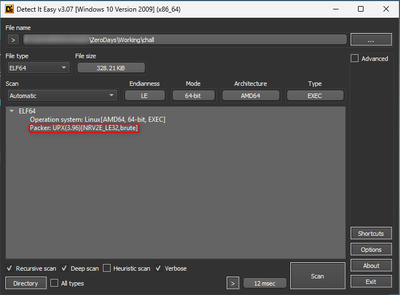
The UPX packer/unpacker can be downloaded to unpack the file. You can find it here.
The following command can be utilized to unpack the UPX packed file -
upx.exe -d [Filename]
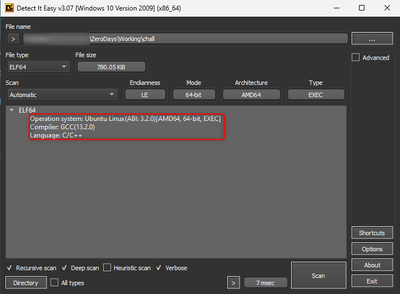
Upon reevaluation using Detect-It-Easy, it is observed that the file is now unpacked, resulting in a clean binary.
Upon opening the file in Binary Ninja and navigating to the main function, the flag string is observed.
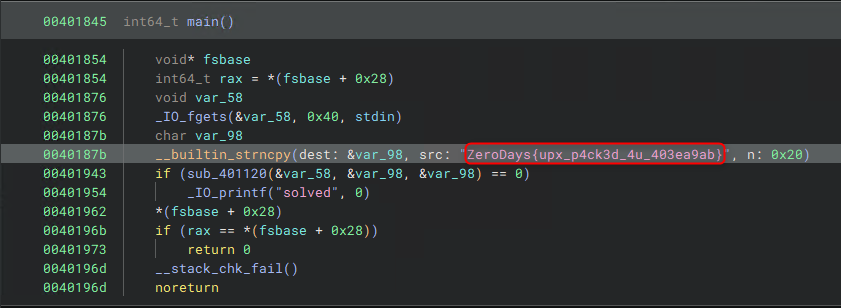
The acquired flag is as follows -
Flag - ZeroDays{upx_p4ck3d_4u_403ea9ab}