Zero Days CTF (2024) RE - 1
Embark on the inaugural reverse engineering CTF challenge, 'mystery.pyc', to unravel Python's .pyc file intricacies. Explore compiled bytecode and decompiled output, culminating in flag reconstruction using CyberChef.

For the first Capture The Flag (CTF) challenge, participants are presented with a singular file named 'mystery.pyc'.
In Python, .pyc files represent compiled bytecode generated by the interpreter upon script import or execution. They facilitate direct execution by the interpreter without recurrent source code compilation, thus enhancing script execution speed, particularly for substantial scripts or modules. Once generated, .pyc files render .py files unnecessary unless subsequent edits are required.
Attempting to open a .pyc file in a text editor does not reveal any readable data or code.
The decompilation of this .pyc file into source code will be conducted using a tool called pycdc, accessible here.
Upon downloading the project, the instructions provided in the project's readme are followed to build the project and acquire pycdc.exe.
To execute pycdc in accordance with the readme instructions, utilize the following command format -
./pycdc [PATH TO PYC FILE]
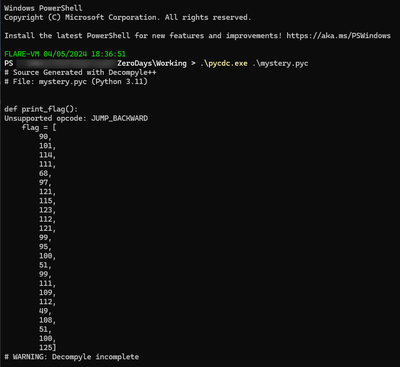
This yields the following decompilation output -
def print_flag():
Unsupported opcode: JUMP_BACKWARD
flag = [
90,
101,
114,
111,
68,
97,
121,
115,
123,
112,
121,
99,
95,
100,
51,
99,
111,
109,
112,
49,
108,
51,
100,
125]
# WARNING: Decompyle incomplete
The observed output comprises valid decimal representations convertible to ASCII characters. This can be effectively employed for flag reconstruction in CyberChef, specifically utilizing the "FromDecimal" function.
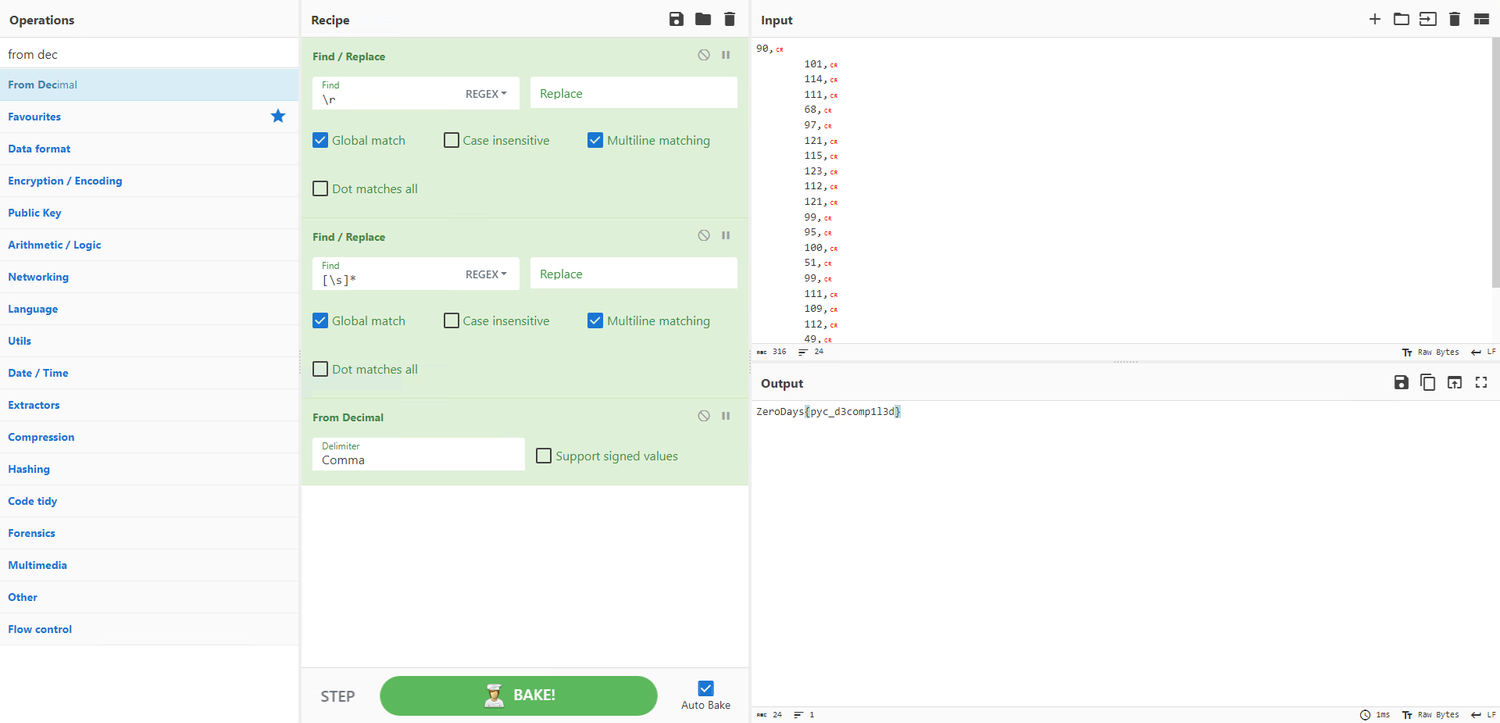
This results in obtaining the flag. The acquired flag is as follows -
Flag - ZeroDays{pyc_d3comp1l3d}